Technology has changed the way people work, communicate, buy and even pay for goods. Businesses and consumers do not always prefer cash. This behavior is giving way to contactless payment systems, such as Apple Pay. Thanks to the spread of the use of phones, consumers pay for their items in digital cash registers. Currently, there is a new payment system in development: the cryptocurrency. And that’s why the Cryptocurrency wallet development service is increasing day by day.
Today we have all heard about bitcoin. This was the first cryptocurrency that became known. But there are others that are gaining increasing popularity. There are more than 2000 different types of cryptocurrencies that increases every day. Here we explain all about Cryptocurrency and Cryptocurrency wallet development service companies.
According to research, it is estimated that most people have heard about cryptocurrencies. But do not understand their meaning. So, what is a cryptocurrency, what is its level of security and how can it invest in this market? Below, you will find a series of answers to your concerns. Consider them as basic aspects of cryptocurrencies.
What is a cryptocurrency?
The cryptocurrency is a digital payment system. It does not depend on banks to verify transactions. It is a peer system that allows anyone to send and receive payments to and from anywhere. Instead of physical money, cryptocurrency payments exist.
Only in the form of digital inputs, it directed to an online database. In which specific transactions are well described. When cryptocurrency funds are transferred, transactions recorded in an accounting record. The cryptocurrency is fast stored in a digital wallet.
The cryptocurrency called the way that uses the encryption mechanism. It verifies the transactions as well. This means that there is an advanced coding in the storing. And Also in the transmitting process of cryptocurrency data. They are between digital wallets and accounting records. The purpose of encryption is to provide security and protection.
How safe is the cryptocurrency wallet?

Cryptocurrencies are well shaped by blockchain technology. The blockchain describes the way in which transactions recorded in “blocks”. This is a complex technical process. But the result is a digital accounting record of cryptocurrency transactions. It is difficult for hackers to fake. That’s why the cryptocurrency wallet development service is growing day by day.
Also, transactions need a two-factor authentication process. For example, you may ask to enter a username and password to start a transaction. Next, you may need to enter an authentication code that is must send in a text message to your personal phone.
Although there are well-established security mechanisms. This does not imply that cryptocurrencies cannot be over violated. In fact, many pirate attacks have cost cryptocurrency startups a lot of money. Hacker attacks on Coincheck and BitGrail perpetrated in 2018. It resulted in losses of USD 534 million and USD 195 million. This makes them two of the biggest cyber hacking attacks of 2018.
Cryptocurrency wallet service tracks the secret keys which used to cryptocurrency transactions. It is a piece of transaction software. There are many crypto wallet development service company presented now. They can serve an easy and secure transaction with a personal key. With these keys, the owner can prove himself as his own assets. The cryptocurrency ecosystem executes the transactions that the owner can transfer. Also, he can change them in his own ways. These are the cryptocurrency ecosystem fundamentals.
In cryptocurrency, crypto wallets are like the function keys to the blockchain car. The blockchain car will not start without those function keys. As like this, there are no other ways to prove the ownership of the owner to a digital asset.
Does the Crypto wallet makes a secure transaction?
A crypto wallet keeps track of the encryption key that may be used for transactions. Also, it keeps the address stored where individual assets occupy in a blockchain. The owner may lose control over all his digital currency (money) or assets if he loses that address.
Hardware wallet and software wallet: are two main crypto wallet types. They are also known as cold and hot storage crypto wallets. Through a fast Internet service, you can access with hot storage wallets services. Such as Coinbase. It is one of the biggest cryptocurrency exchange services. Also, they provide digital wallets for online users. They can manage the online and client-side wallet services for future transactions. Also, it can be further managed on a user’s mobile device or computer.
With cold storage crypto wallets, you can access offline on a smartphone or a USB drive. Just download it on your devices. For example, Exodus.io and Dash QT. They are the two big cold storage crypto wallet service provider. Also, you can buy it as an online transaction device. Here the crypto wallet software already installed. These types of wallet devices are sold more by suppliers such as Ledger and Trezor.
You can divide the hardware wallet into crypto-assist type storage wallets. It handles arbitrary data keys and signatures. They are sometimes referred to as hardware security modules (HSM). It handles the online generation and the signing of complete transactions. Then this sent that to the distributed crypto wallet accounting network.
Communicating with the blockchain, the hardware communicates through the codes on the device. But, it is not a very friendly user interface.
Hot and cold wallets, which ones are safer?
A cold storage wallet is safer than a hot wallet because it is not connected to the Internet. Most cryptocurrency attacks have occurred when a hacker attacks an online wallet service. And transfers the secret keys to his own wallet, transferring the associated funds.
For example, the Japanese online crypto wallet exchange services. In 2014, Mr. Gat was stolen from its hot wallet of 850 thousand bitcoins valued at more than 450 million dollars. And in 2018, the Coincheck bitcoin wallet development service suffered a robbery. Almost one billion dollars in cryptocurrency from its hot wallet service. Many small thefts have occurred in the last five years, through online wallet hacks.
There is a common attack vectors. It used to steal funds from blockchain cryptocurrency accounts. That is [an] acquisition of customer accounts. This is the main reason why we recommend not storing cryptocurrency balances. Many cryptocurrency wallet development services also provide this before your transaction. Bitcoin MLM software service may not apply this. But you have to know this.
How to strengthen the security of crypto wallets
Gartner recommends converting cryptocurrency into fiat money – cold cash. Such as real dollars, euros, yen or some other currency – to secure it. Or keep cryptographic keys in a cold wallet. The latter means, then, making a paper copy of the keys. And keeping that paper in a safe place. You can secure it on bank safe deposit box.
Paper wallet can also be used as a type of online wallet through software that creates a QR code. So that can be scanned to allow blockchain transactions. Push technology links the second factor to a registered mobile phone. So that only an owner’s phone can approve access. That request rejected by the exchange wallet authentication service.
Centralized wallet services have been lucrative goals in the past. Because hackers could get millions of dollars in cryptocurrencies in a few minutes. But, cryptocurrency hackers have also stolen the SIM identity of a mobile phone. It is done with a phone wallet.
These include “SIM exchanges”. In which a thief registers an existing number on your phone. So that notifications or push messages are sent to that phone, rather than to the rightful owner. Hackers do this through the social engineering of mobile phone customer service representatives.
Ledger Nano S USB cold storage crypto wallet.
There have also been cryptocurrency thefts through malware placed on an owner’s device. That allows the theft of their secret keys.
“There are ways to mitigate all these attacks. But the best solution so far is to use some kind of hardware wallet. And also have a backup of your secret keys somewhere safe. The most difficult part of bitcoin wallets is the security of data. They are responsible for the secure storage of small and confidential data.
Most people are not familiar with the levels of security and paranoia. Those are must require to defend against people determined to steal their keys.
The danger of losing your keys
There is a problem with a cold wallet. That is if you have not backed up the information, or kept a hard copy of it in a safe place. You lose that device, Loses your digital assets forever. You no longer know where your cryptocurrency resides in a block chain. Or you have the keys to authenticate that you are the owner.
Hot storage wallets, but, have the advantage of service provider support. If you lose your wallet access code, there are questions that will allow you to recover them.
There are many limited methods to recover private keys in a cold storage wallet. That has lost and, in general, they are not easy to use. For example, Coinbase allows users a restoration mechanism. It consists of 24 random word recovery phrases. So that users must record when they create their wallets.
Blockchain accounting books work based on a consensus mechanism without trust. That’s means that you do not need to know the person or people with whom you are making transactions. A distributed accounting book will rely on any transaction signed by a valid secret key. That is why it is so important to protect the keys.
The wallets are very intended to store those keys. To make the digital signature necessary for the distributed ledger, accept the transaction.
Crypto wallets uses: Digital Currency
The vast majority of crypto wallet applications are also used to store cryptocurrencies. Such as bitcoin, Ethereum, Ripple or Litecoin. The software can also store the keys of fungible and non-fungible digital tokens. It represents goods, financial assets, securities, and services.
For example, a wallet token stored in a crypto wallet could represent concert or plane tickets. Unique works of art or products in a supply chain. Also, virtual anything with a digital value attached.
All accounting books distributed with decentralized consensus mechanisms. They all are based on the capacity security model. The possession of an encryption key approved with a digital signature. And authorizes the action that represents the transaction.
Then, any application modeled in a distributed ledger requires users to have wallets. They use it to sign transactions that work for that application. For Bitcoin, transactions only transfer bitcoins to another encryption key. And to another wallet owner. They sign transactions that track the asset for things like a supply chain.
In the future, a new “untrusted” global economy could be based on crypto and blockchain wallets. It allows everything from financial and professional to individual histories. Also, your tax information, personal medical information or your consumer preferences to corporations. This will maintain employee digital identities or partners and control access to applications.
Digitized representations of traditional identity documents. Personal documents such as driver’s licenses, passports, birth certificates. Also, social security cards, voter registration information, and voting records. It can also be stored in crypto wallets. It gives owners Control over who has access.
And make those crypto wallets even more valuable and make it even more important that they be safe.
The wallets, purses private keys needed to access the balances recorded in an address. Or public key corresponding chain blocks and spare power. There are currently several types of cryptocurrency wallets. It can be categorized using two variables: ease of use and security.
Types of crypto active portfolios, categorized by security and ease of use.
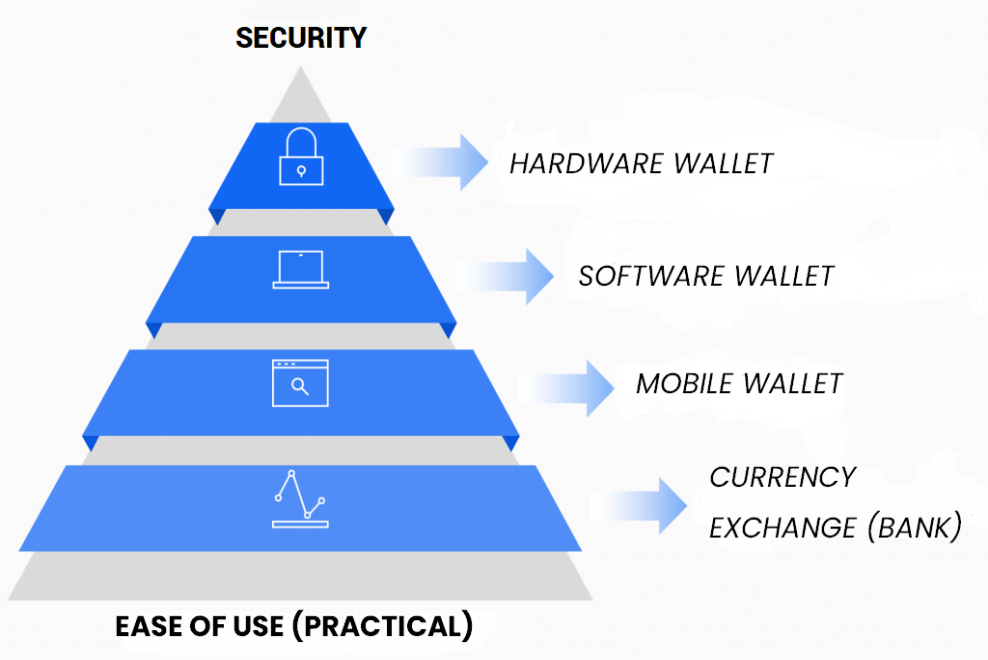
At the tip of the pyramid, shows are the safest and most difficult to use wallets. While at the bottom are the easiest to use, but also the least secure. The pyramid also represents the adoption in the use of each type of portfolio. Those of the fund are used, while those of the top is not as used.
A contradictory condition of the crypto wallet ecosystem. Given the fact that it is money that we deal with. Security is a determining factor in a good crypto asset portfolio.
Starting at the bottom of the pyramid. There are exchange houses, which act as a cryptocurrency bank. Users enter their cryptocurrencies at an assigned address. And the “bank” handles managing them. That is, they move users’ money to one or more central wallets. And from there they carry out the payment or sale that their customers state.
They are useful for the exchange between crypto-assets and fiat currencies. But, these services are prone to hacking, scam, service outages and other risks. So users’ money may be unavailable or disappear. Besides, they usually change the conditions of use at their sole discretion. They cause account closures and other inconvenience to users.
Some cryptocurrency wallet development exchange services are Coinbase, Bittrex, Xapo, and many others.
Cryptocurrency Wallet Development Services and Exchange Policy
The exchange houses represent a business that allows the encounter between two currencies. The real world (physical currencies) and the digital world (cryptocurrencies). Although there are also those between crypto-assets. Users who store their savings on these services are at risk of losing their money. Advances such as Atomic Swaps will make their use unnecessary in the future. It will happen with the bitcoin development services.
A step further up the pyramid are online wallets. Websites that allow users to mobilize their money. Having exclusive control of their private keys. And without having to install any software. In this type of purses, an abstraction of the private key is well generated in the form of 12 or more words. It’s called seed or backup that must be noted by the user on paper. Or other resistant medium and outside of line, to safeguard your money.
In online portfolios, the probability of hacking user funds decreases. Even though it is not zero. Since a hacker could install some malicious code on the website. And steal the seeds of users accessing the page. The unavailability of funds remains a problem in these purses. As they may suffer from temporary falls for various reasons.
Blockchain.info and MyEtherWallet are two of the most used online wallets.
Security under Cryptocurrency Wallet Development Service Company
In the penultimate step of the pyramid are the wallet applications. Software that can be installed on computers and/or mobile devices. And serve as an interface to display balances in the addresses that the user owns. And mobilize the money in them. They can generate a new seed or use a before created backup. As well as allow the activation of an extra code or key, at the software level, to mobilize money.
These applications cut the problem of the unavailability of money. It means unless the device is damaged or not with the software nearby. And transfer the responsibility for security to the user. He must keep his device free of viruses, refraining from entering insecure pages. Also, to connect to free Wi-Fi networks and to insert any unknown peripherals. Such as pen drives or external hard drives, into the system.
Examples of portfolio applications are Exodus, Jaxx, Electrum, Mycelium, Coinomi, and Bitpay.
At the top of the pyramid are the hardware purses, also called cold wallets. It indicates the physical devices. That house the private key of the associated offline accounts. It allows transactions to you sign without exposing the seed. These wallets are like a flash drive. They are all connected via USB to the computer and represent the safest way to protect crypto assets. These devices allow cryptocurrencies to send even in insecure environments. Such as outside computers.
The hardware wallets are the only ones that generate a direct cost for the user. Their prices vary but can get from $ 50 onwards. Some well-known crypto wallet brands are Ledger, Trezor, KeepKey and Digital Bitbox.
Essential characteristics of a cryptocurrency wallet
Control over money: Cryptocurrency wallets can allow individual handling. It means only the user owns private keys. Joint management means the owner and the company own private keys. Or by a third party that the company owns the keys private of the money stored in them. Depending on the control over the money management chosen, the security measures. It indicates the responsibility and control of the user. Also the security of the funds in the portfolio increases and decreases.
Validation: Cryptocurrency wallet can be used to confirm the transactions made. Complete validation indicates a complete node, download the entire blockchain. Simplified validation measures single node, only download the hashes of the block. And centralized validation means a complete node from a third party. Based on the type of validation that the purse uses, it must be trusted or not. That a third party performs the correct validation of the transactions made.
Transparency: cryptocurrency wallet can be transparent or not transparent. The application code can be well audited and verified by the user. And the code of the application is closed and the application runs. Depending on the degree of transparency, the user must trust more or less. It depends on it then the application developer did not add secret or malicious codes. It could cause them to lose their funds or be stolen.
Environment: cryptocurrency wallets development services can be installed in vulnerable (virus-prone) environments. With or without two-step authentication. Secure environments such as cell phones in which applications are isolated. And very secure environments such as physical cryptocurrency wallets, gadgets. Depending on the type of environment used, the user must activate crypto wallet mechanisms. Such as two-step authentication and place complex passwords on their wallets. And devises to prevent loss or theft of funds.
Privacy: Cryptocurrency wallet services may or may not reveal their users’ information. Such as the IP address. You can allow or not the use of the Tor browser to prevent other people or companies. It happens to reuse the wallet addresses with each payment. And it causes from associating the transactions with the user’s IP address. The user should be aware of the information he reveals to the network. It depends on the types of privacy that the wallet service provides to the customer.
Some tips to secure your Cryptocurrency Wallet
• Avoid (if possible) the use of online services. When using web clients that generate private keys for you, it is more advisable to save that page. Also, you can generate private keys offline. You can use a site like bit address to generate private (offline) keys. And print a BIP38 encrypted paper wallet from it.
• If you use multiple wallets, some can be used for daily use (for example, lower expenses). And others for storing large amounts of bitcoins. The remaining wallets can be stored offline as hardware or paper purses.
• Make backup copies of your purses, following rule 3-2-1 (3 copies, 2 media, 1 offsite).
• Encrypt your wallet. Most of the services that provide the creation of a paper wallet allow an encryption method. An extra measure would be to divide the keys in an “m of n” manner. Such as Shamir’s secret exchange scheme (SSSS) as in the passcard. The “m” copies of “n” should be used together to synthesize the complete private keys. While the individual copies cannot be compromised, even if they are exposed.
Finally, always keep your Bitcoin software up to date!
